It would be really helpful to make a feature where certain inputs into the form would not be allowed, based off of data that already exists in my data source (I’m using airtable). For example, I do not want to allow for any forms to submitted with emails already contained in a field in a table of my base, and I do not want any names to be submitted that already exist in another field in my base. Further, having some type of error message would be ideal for that. The closest example I could find was here: I've written some code for custom validation for file upload and thought I'd share. I am trying to write this functionality with code write now, but after 10+ hours of working on it, it is proving to be very difficult.
I am encountering this same question: How do I ensure that forms cannot have arbitrary data injected into AirTable single select and multi-select fields? The answer, AFAIK, is that I cannot with no-code tools.
My goal is to pass data into hidden fields via custom url parameters, or use &prefill_{fieldname}=VALUE to preselect an item in drop-down. The problem is that a user can change the value of the custom URL parameter or the value of the prefill_{fieldname}= parameter and that data gets inserted into the AirTable database without any validation. AirTable does not offer a restriction feature on the data itself, neither does Softr.
This is an business and security CRITICAL issue to resolve. Unresolved, this could lead to a variety of DDOS, injection style attacks, disrupt the service, and/or compromise the security of personal information.
Hmm, Restricting permissions on the field seems to additionally prevent from selecting an item from a drop-down. ie not just adding a new value to the list but selecting a valid value for the field to add to a new row.
I am going to go with… no effective solution by service providers.
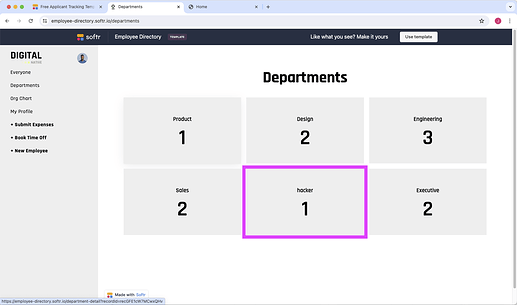
WOW, if you can guess the fieldname on any standalone form page in any of the free Templates, you can pollute fixed site data.
I added a new Department called “hacker” to the Employee Directory sample by putting this in the url and filling out the New Employee form:
You can quickly see how this could be catastrophic for a legitimate business and additionally how this fundamentally changes how forms can safely be used. The risk is that someone starts injecting random categories, tags, filters, etc throughout your site simply by changing a url parameter and submitting a form. I don’t even know where I would start for log investigations to get the identity of a bad actor who found this out and exploited it.
Moving forward, I may only be able to use the built-in modal forms and not any URL forms and that alters my product plan and restricts my feature development.
For Softr.io employees. I am not trying to maliciously hack your site, simply show the extent of the vulnerability. Feel free to delete this post and contact me directly.
Edited 2024-07-08
After much work and testing various scenarios, the solution is as follows…
To prevent Users from injecting data into your AirTable schema by hijacking the prefill_[field_name] feature you must:
- create a “Team” or higher AirTable account plan
- Sign in as the account Owner, eg owner@blah.com
- Invite a new user to the Base you want in AirTable and then sign-in and create the new user in AirTable which is going to be the “API” account which you will bind the personal access token (PAT), eg. apieditor@blah.com
a. Account settings> Workspace Settings for your Base > Add or manage workspace collaborators
b. Select Editor from the drop-down
c. Send Invite - Follow invite email and Sign in as apieditor@
- create a PAT with the appropriate permissions, no special configuration is required at this step (although I do question the schema.bases.write Scope)
- store the PAT for use in Softr
- [IF you did not set the invited user to Editor] returning to the owner@ account, Change apieditor@ collaborator permissions to Editor
a. Account settings> Workspace Settings for your Base > Add or manage workspace collaborators > Manage access
b. Change permission dropdown to Editor - Signing into Softr, navigate to the Root of the dashboard and click Data sources (or from within the App click Settings > Data Sources > … > Manage on the AirTable Data source you are going to change the permissions
- For the AirTable data source you wish to tighten the permissions, click “…” > Re-authenticate
- Follow the workflow replacing the old for the new Personal Access Token (saved in step 6) and Done!
This will replace ALL existing configured blocks connected from wide open permissions to the new more restricted API access token.
Note: as of mid-2024 moving to an AirTable team plan will cost $240 per seat annually. To support this improved security feature you will need 2 seats at $480 annually, total.